I recently obtained the Offensive Security Exploitation Expert (OSEE) certification and wanted to write a review on both the exam and the Advanced Windows Exploitation (AWE/EXP-401) course itself. Perhaps even more importantly I wanted to write about my key takeaways. If you’re just interested in preparing yourself for this course, I have released all my prep resources which can be found on my GitHub repository AWE-PREP. However, this review will provide context as to why I selected these resources for prep.
In this review I will be talking about multiple courses not just those created by Offensive Security. It’s imperative that you see the full picture of the journey since it is not linear and frankly everyone’s journey is different. More than likely my path will differ from yours.
Let’s kick things off…
Table of Contents #
- Going To London
- The Consequences Of My Own Actions
- Ramblings of a Madman
- Ain’t No Rest for the Wicked
Going To London #
AWE is offered at multiple locations such as Black Hat USA. However, I had been trying to take this course since 2019 so I wanted to pick a date that allowed me to prep sufficiently. The date that made the most sense for me would take place in London. If you get a seat, before you arrive you will get a series of emails containing links to publications that can help you get familiar with some of the information that will be covered in the course.
My first email containing this information was 11 days before the start date and the links provided contained information you should already be familiar with (in my opinion).
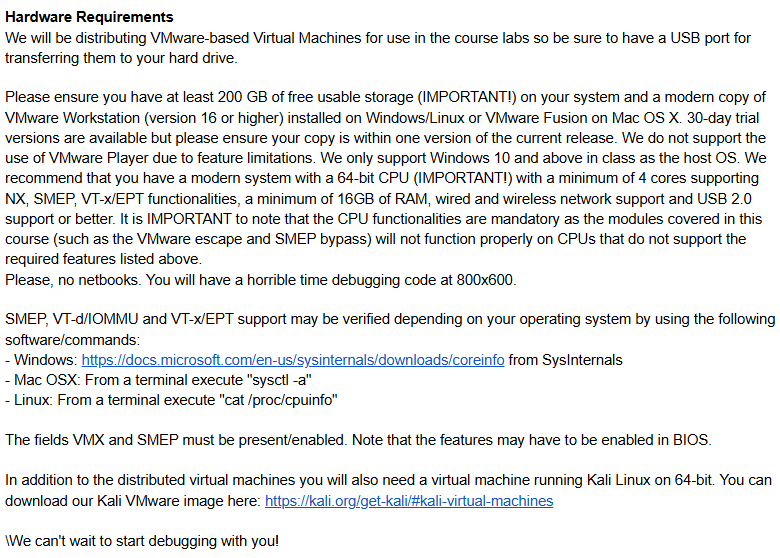
Perhaps more importantly, you get a list of hardware requirements to be able to participate in the training itself. Since this is a bleeding edge course, I imagine that these hardware requirements will change over time but stay relatively the same.
I would advise against bringing anything that uses an ARM processor!
About three days later I received another email containing more articles. This time you may see material you are not familiar with - my advice is to read what you feel will be necessary to understand a broad set of subjects, but don’t overwhelm yourself. It’s easy to get “fear” from reading these articles thinking AWE will be worse. The reality is that these articles may not go into as many details as Offsec will, so consume the material understanding you may not fully understand it… yet.
Course Overview (2024) #
I took this course in 2024, this is important to mention since this course is constantly updated. As of 2025 the course material has already changed but for the sake of this review the following material was covered when I took the AWE:
- Custom Shellcode Creation
- VMWare Workstation Guest-To-Host Escape
- Microsoft Edge Type Confusion
- Driver Callback Overwrite
- Unsanitized User-mode Callback
This is a very high-level overview of the material covered but ultimately there’s a lot that goes into each of these five categories. Expect to learn how to bypass most modern exploit mitigations such ASLR, DEP, CFG, ACG, CET, and even exploit mitigations that are optionally enabled.
Since this course updates so frequently I will avoid talking about anything specific to these sections.
Milking the Course #
Before starting the course, I had already completed RET2 System Wargames and HackSys Extreme Vulnerable Driver (HEVD) so a good amount of the information was fairly easy to digest. Of course, there were things I did not know or fully understand at the time but ultimately the confidence I gained from these two prep resources made me significantly less intimidated. I mention this to emphasize that knowing C and Assembly will take you further than learning techniques. In fact, the “Violet Phosphorus” technique I developed I did so with just research on how kernel Page Table Entries (PTE’s) work. Offsec bypasses SMEP using a different technique within the course.
That said, if you follow this path, you will likely feel just as confident. However, don’t be fooled by this feeling, the course requires your attention and to get the most out of it DO NOT FOCUS ON ANY OF THE EXTRA MILES UNTIL AFTER THE DAYS TRAINING HAS ENDED.
If we do some quick math, assuming the course is 10k, you are paying 2k per day. If you work on any extra miles during the training like I did, you will literally be missing out on 2k… Thankfully I was not the only one who did this or I would feel even worse than I did - the motivation was a challenge coin which in the end I did not even get… Funny enough If I would have paid attention on one of the training days, I would have learned what was needed to get a coin. So, pay attention!!! You are there to learn!!
In addition to losing out on learning techniques for a coin, I missed out on learning information that would have resulted in questions. When you get home, you’ll see not everything is explained thoroughly and you’ll need to fill in the gaps. If I had paid attention during the training I could have asked these questions in person.
The Consequences Of My Own Actions #
When I got back from London, I realized that I pretty much ignored half of what was presented during the course. Learn from my mistakes!
Sadly, around this time I also entered a new role as a Security Researcher in which I would be utilizing ARM/AARCH64 more than x64. This meant I would need to juggle 3 architectures and multiple languages (Java, Python, C, C++, etc). A few months after this I would also have my Arsenal Talk be accepted for Black Hat USA 2025 - so I needed to work on my tool Sickle as well.

Clearly, I had my hands full, but I wanted to get the OSEE so if I wanted to transition into a Windows Reverse Engineering role or work as a Windows Kernel Exploit Developer, I would have the knowledge needed to get past any hurdles that come with the interview process. Since in my experience, I can (like many others) figure anything out with enough time. However, should I fail an interview task, the OSEE will be a good indicator to employers of how hard I’m willing to work on complex tasks.
This meant I had to work on this whenever possible and could not be as heads down as I would be on a course relevant to my position. Really thinking about it though, everyone is constantly doing stuff, so even though you may not be in the exact same boat you’re likely in a similar situation (family, friends, wife, kids, work, etc). That said I documented exactly how much time it took me to complete the course on my own from start to finish.
Course Timelines #
Below is a table of how I progressed through the course from start to finish. It’s important to note I treated the course as if I were taking the exam - this meant everywhere IDA was used Ghidra was used instead! This likely added a significant amount of time but I truly believe it was worth the time investment.
| Section | Time Taken To Complete |
|---|---|
| Custom Shellcode Creation | 8 hours, 20min |
| VMWare Workstation Guest-To-Host Escape | 73 hours, 48min |
| Microsoft Edge Type Confusion | 80 hours, 25min |
| Driver Callback Overwrite | 65 hours, 22min |
| Unsanitized User-mode Callback | 46 hours, 34min |
Based on the table shown above, the course alone took me about 274 hours to complete from start to finish with a “generic” understanding of the subject matter. Unfortunately, at the time of passing the OSEE I did not finish all the extra miles.
I did however document how long they took me! Below is the table of extra mile timelines per section:
| Section | Time Taken To Complete |
|---|---|
| Custom Shellcode Creation | No Extra Miles |
| VMWare Workstation Guest-To-Host Escape | 35 hours, 41min |
| Microsoft Edge Type Confusion | 51 hours, 52min |
| Driver Callback Overwrite | 28 hours 2min |
| Unsanitized User-mode Callback | N/A |
This meant it took me a total of about 115 hours. So, let’s say total time before the exam spent on the AWE was about 389 hours. If I did not have as many distractions I absolutely would have invested more time in the overall subject matter.
My Approach #
When approaching any course my objective is to learn not get a certification. If you follow this sentiment, my advice is to complete the course section and generate a list of questions for yourself. Since the AWE is constantly evolving, I won’t include all my generated questions but below are a few.
| Description | Complete |
|---|---|
| Offsec used X to implement Y. Can we implement Y without the use of X? | [✔️] |
| Offsec used X to bypass Y when exploiting Z. Write a standalone PoC to exploit this outside of Z, if the PoC works write a function to abuse this, so that it can be integrated into future exploits. | [✔️] |
| Create a diagram showing a high-level overview of Z exploit, ensure you understand each part of the exploitation process. | [✔️] |
| On page X Offsec traversed Y, ensure you understand why. | [✔️] |
In addition to this go the extra mile on challenges that are not necessarily an “extra mile”. As a high-level example, if you are given the challenge:
Challenge: Write a for loop
Don’t write:
for (int i = 0; i < 5; i++)
{
printf("hi\n");
}
Instead, write something that needs a loop. This way you learn the concept but more importantly you learn how and when to use it. Because I study this way, there were times within the AWE I completed an extra mile BEFORE I knew it was going to be one. I believe this helped me understand the subject matter more than someone who only did the challenges as presented to them.
That said I did not complete all the extra miles, mainly due to the fact I was also working with ARM in parallel (taking additional training). If you can, I heavily recommend completing all extra miles!
Exam #
I sadly cannot reveal too much on the exam itself, but I can say that it is rather “fair” in terms of the challenges. Having worked as an Exploit Developer / Security Researcher it was very similar to a task you may be given on the job. That said, they don’t expect you to take the 0day angle - that’s all I’ll say in terms of the actual content the exam consists of.
Unfortunately for me, I had not touched WinDbg for weeks prior to the exam (GDB had me pinned down and AARCH64 was right next to him kicking me). So, the night before I gave myself a quick refresher and got re-acquainted with where everything I had written was (tooling).
Overall, despite this I still felt confident in my abilities to get the OSEE.
Take 1 #
So, the day of the exam had arrived and after reading the questions I still felt like I could do this. However, the biggest mistake I made in the first 16ish hours was jumping back and forth between the challenges - my advice to you is to take your time on one challenge at a time.
Sadly, in the end I did not automate one thing as effectively as I could have costing me the exam.
Take 2 #
My second attempt I pretty much got half the points needed to pass within a few hours (the proctor ended up thinking I was cheating lol). A few hours after that I had enough points to pass (but I did not know that).
So, I proceeded to waste (I’m willing to bet) 30 hours trying to make something I already had working “stronger”.
Eventually, I thought to myself “nahhhh I reverse engineered this entire thing… this is not possible”. So, I asked the proctor a question about the challenge I was working on, and they came back and replied:
NOT EXACT QOUTE: "We cannot answer questions in regard to the exam"
So, I re-read the question and that response, then I thought to myself - “wow… I had this in the first X hours”. I looked at the time and thought to myself, I hope this is enough to pass because I still need to write the report…
Luckily for me, this time I had survived the exam:

Exam Advice #
Having passed, if I could talk to my past self this is the advice I would give:
- If your exploit works in the lab but not the target - let it run… the target environment may be slower
- If compilation fails and you are using a share, compile outside the share
- Automate the debugging process as much as possible (crash, launch, attach, etc)
- Do not re-use variable names even across functions (encountered weird issues)
- Don’t initialize variables you need for exploitation (encountered weird issues)
- e.g
LPVOID thing = func();is better thanLPVOID thing = NULL; thing = func();.
- e.g
- If exploitation is unreliable a simple
Sleep()can make a huge difference - Try not to error check, some functions return partial data and still trigger an error but that partial data could be all you need
- Do not use WinDbg preview unless you have no choice (have seen debugging functionalities not work)
- Process context matters, especially with breakpoints
- If the exploit worked fine but randomly stopped working revert the lab
- Use the same target language for compilation as you did during the course
- e.g don’t use C++11 when you have been compiling your code in C++17
- Backup, backup, backup
- e.g if you make considerable progress copy the current exploit to a backup then continue working
- e.g if you write a function but found it to not be useful create a backup (may come in handy later)
- Take your time, if you don’t see something immediately make a judgment call on time usage and reverse engineer!
- READ THE CHALLENGES CAREFULLY
Ramblings of a Madman #
I first got introduced to binary exploitation like many others with a JMP ESP when learning about buffer overflows. More specifically, I did so using the Immunity Debugger within the now retired OSCP.

Now I know what you’re thinking… what the frick is an Immunity Debugger? For the sake of time, it’s just an x86 debugger developed by the now dead Immunity Inc (R.I.P). An image of it can be seen below.
I mention this for multiple reasons but perhaps the most important being - technology is constantly evolving and true understanding is necessary to continue to evolve with it. At the time of writing a Buffer Overflow I had no idea what I was doing… yet I still passed the exam since I learned the steps taken when exploiting this very specific flaw. Knowing these steps, I could exploit any buffer overflow assuming it had no memory protections and the right conditions…
Younger me being incredibly confident in my abilities (I was OSCP certified after all), was quickly humbled by a user on NetSecFocus (we’ll call him Jack) who was an actual reverse engineer not a penetration tester. In fact, if I remember correctly, he had NO CERTIFICATIONS just a love for mathematics.
To make a long story short after an argument with Jack over what occurs during the exploitation of a stack overflow I learned a few things:
- I could exploit a bug under very specific conditions
- I knew what steps were needed
- I didn’t know why or how this was possible
I needed to know more… so I made a goal for myself… which looking back is ambitious for someone who didn’t even understand what the stack did…
I wanted to become an Exploit Developer.
My Path to OSEE #
Before I dive deeper into my rant(s) below is a high-level overview of my accomplishments before getting the OSEE. Please keep in mind I have only included information relevant to this course, so I won’t be focusing on anything that I don’t believe is relevant to exploit development. The reason I want you to see this is so that you understand that depending on your goal you do not need the OSEE certification. This is not said to deter you from taking AWE either - in fact I believe that each time the course is updated you would benefit from retaking it (regardless of obtaining the OSEE) and I will explain why within this review.
The main takeaway from this roadmap is to take your time and not focus on achieving the OSEE. Instead focus on actually learning!
| Date | Objective | Return on Investment |
|---|---|---|
| 2016 | C The Absolute Beginners Guide | - Exposure to a compiler - Exposure to fixing basic bugs |
| 2017 | OSCP | - Introduction to debuggers - Introduction to stack overflows |
| 2017 | SecurityTube Linux Assembly Expert (SLAE) | - Introduction to GDB - Better understanding of assembly |
| 2017 | Sickle | - Mainly developed for formatting custom shellcode |
| 2017 | Corelan Exploitation Series | - Finally understanding stack overflows - Introduction to SEH based exploits - Introduction to unicode exploits (SEH) - Introduction to egghunters - Introduction to shellcoding |
| 2017 | Vulnserver | - Introduction to fuzzing (boofuzz) - Practicing SEH based vulnerability exploitation - Discovered 0day shorty after using new skills |
| 2017 | Cracking the Perimeter (CTP) / OSCE | - Introduction to backdooring PE’s - Introduction to AV bypasses - Introduction to ASLR - Introduction shellcode magic (Aaron Adams) - Introduction to ASCII encoding |
| 2019 | Advanced Web Exploitation Expert (AWAE) / OSWE | - Introduction to source code review - Exposure to multiple languages - Exposure to exploit primitives - Developing large complex exploits |
| 2019 | Corelan Advanced Exploit Development Training | - Introduction to windows heap - Introduction to use-after-free vulnerabilities - Introduction to heap exploitation - Introduction to browser exploitation - Exposure to ROP |
| 2019 | 0dayz (IBM) | - Hit @midwestneil with a “trust me bro” for research time - First time using IDA Pro - First exposure to reverse engineering an x64 target - Reverse engineered the server, client, and protocol - Created a custom fuzzer (from scratch - boofuzz failed) - Discovered 2 RCE’s and 1 DoS - Exposure to responsible disclosure - No profit ( ㄕཀ ʖ̯ ཀ) |
| 2020 | Deeper dives into C | - The C Programming Language - Effective C - Learn C++ |
| 2020 | SANS 760 | - Exposure to IDA scripting - windows Internals Knowledge - ROP/JOP - ASLR - Canaries / Cookies - Overall I was humbled… |
| 2021 | CodeMachine WINMAL Course | - Programming using the windows API (C/C++) - Exposure to advanced malware techniques - Implant Development - Persistence - Process Injection - Evasion techniques |
| 2021 | Evasion Techniques and Breaching Defenses (PEN-300) | - Programming using the windows api (C#, JS, VBS) - Process Injection Techniques - Antivirus Evasion |
| 2021 | Modern Binary Exploitation (MBE) | - Learned reverse engineering tooling - Learned exploitation techniques - Learned about a few memory protections - Exposure to linux kernel exploitation |
| 2021 | Immunity Inc | - Briefly worked as a Senior Exploit Developer - Humbled daily |
| 2024 | N/A | - Briefly worked as a Principal Offensive Security Researcher |
| 2024 | The Ghidra Book: The Definitive Guide (to page 256) | - Learned how Ghidra works (applicable to IDA / other tools) - Actually learned how to RE effectively |
| 2024 | RET2 Systems Wargames | - Rehashed C fundementals and learned new things! - Understood vulnerabilties better since we see the C code - Exercised reverse engineering - Exposure to multiple memory protections - Exposure to unique flaws (not vanilla) - Utilized imaginitive ways to exploit complex challenges - My first exposure to race conditions (and I understood them!) |
| 2024 | Learn C++ | - Learned C++ from an online platform - Gained a deeper appreciate for C |
| 2024 | HackSysVulnerableDriver (HEVD) | - Practiced what I learned from RET2 in the kernel - Hit a roadblock and wrote Violet Phosphorus ROP chain - Learned my technique is a SMEP bypass NOT a VBS bypass |
| 2024 | Advanced Windows Exploitation (AWE) | - Custom shellcode creation - Introduction to virtual machine escapes - Introduction to chakra internals - Exposure to default and non-default enabled mitigations - Driver vulnerability exploitation - Native callback vulnerability exploitation |
| 2025 | OSEE | - Completed the exam |
Recommended Path #
So clearly, I had the huge privilege of being able to afford some of these courses. This is because shortly after obtaining the OSCP and OSCE I was hired on by IBM as a Cloud Red Team Operator. I believe the SANS 760 was the first course I had the privilege of being sponsored, regardless you may be in a position where you fund your own training.
So where do I recommend you invest your time and money? Before answering, please keep in mind that I have never taken the Windows User Mode Exploit Development (EXP-301 / OSED) from Offsec since I previously took the now retired OSCE.
Although EXP-301 covers newer material compared to that of the OSCE I learned most of what I know today from other sources. In my opinion, this further emphasizes why these certifications NEED to be for life. I believe every OSCP / OSCE student likely continues studying - they just may not necessarily study material on a syllabus.
Regardless, in my experience reverse engineering and the thought process behind exploit development is more important than one platform (Windows or Linux). To focus on techniques (such as the Stack Overflow) will lead you down a path where you will always depend on others to develop your own hacks.
Can you imagine finding a Stack Overflow before anyone knew it existed? This is only possible if you can know how systems works - like our friend Jack.
Shown below is my revised map.
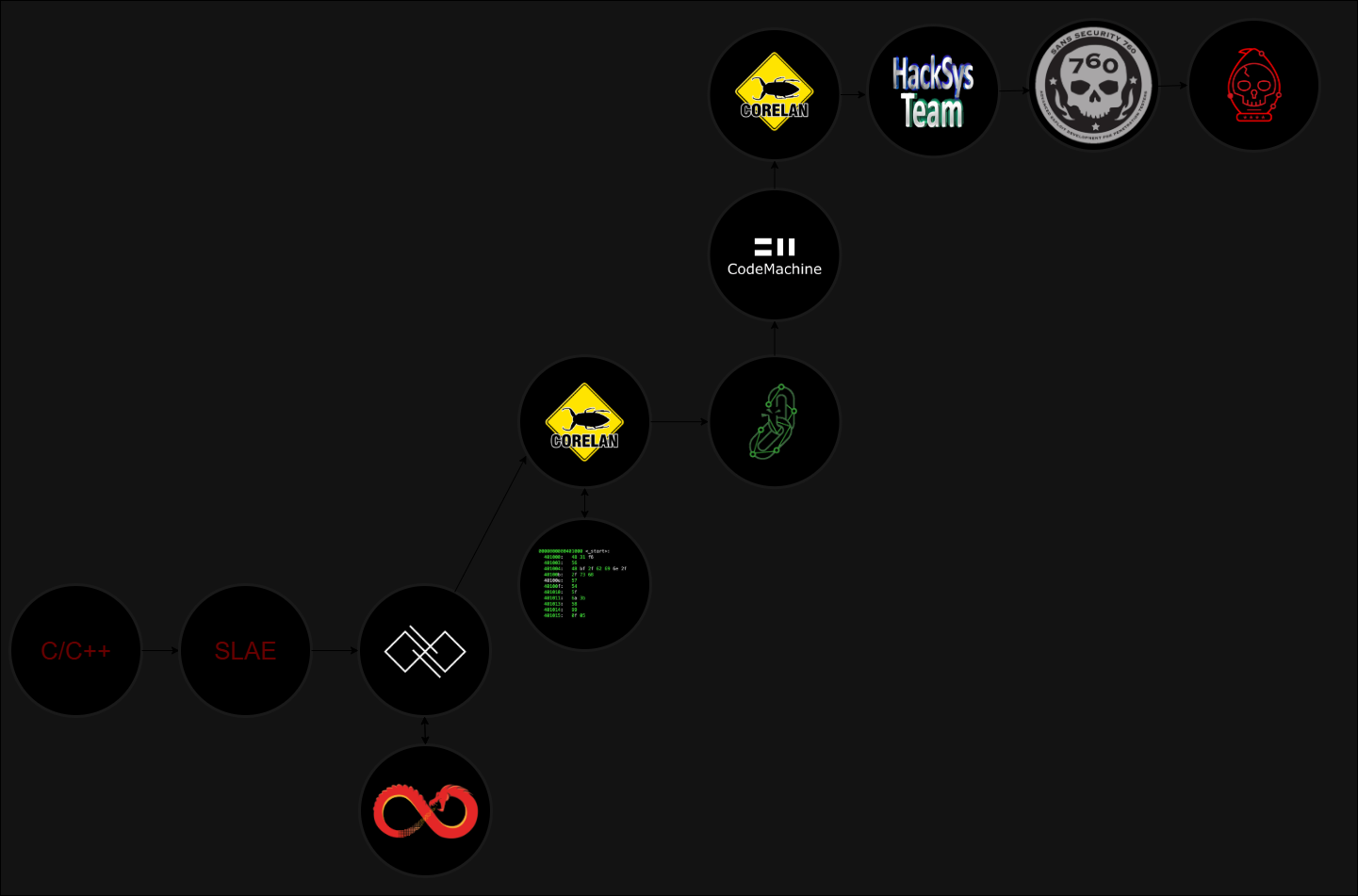
Let’s break this down.
- C/C++
- If your goal is to become a Security Researcher or an Exploit Developer you must learn C. This is not negotiable, the lack of C programming will severely limit your ability to understand any system internals. Windows and Linux are primarily built on C! C is not a vulnerable language like many like to preach it is, the problem is many programmers do not know what they’re really doing which leads to bugs.
- SecurityTube Linux Assembly Expert (SLAE)
- I cannot emphasize this course enough, I believe there is a SLAE64 as well which covers x64 vs x86. If so, take SLAE64! Regardless, this is the best way to get comfortable looking at Assembly Language. I read a good portion of the book Assembly Language Step-By-Step Programming with Linux and I barely started coding in ASM after hundreds of pages… Thankfully abatchy shared SLAE with me or it would have taken an eternity for me to learn assembly.
- RET2 System Wargames + Ghidra Book
- The Ghidra book really helped me level up my reverse engineering capabilities, and I got really comfortable with Ghidra. The best takeaway from the book has to be that the authors tell you how Ghidra can generate disassembly and pseudo code. This helped me develop a mindset on how to view assembly when reversing.
- Taking that knowledge to RET2 made everything click. This is because RET2 provides source code (sometimes), which allows you to really understand what is happening at a C level to then be able to map it to assembly. This is important because in real life sometimes pseudo code is wrong and you the reverse engineer must fix it! This is possible because you are debugging using their online interface (which operates just like GDB). Meaning you cannot escape assembly even with the C code. In addition to this RET2 starts from binaries with no memory protections all the way to Race Conditions with exploit mitigations enabled. As someone with some experience at the time, I actually did learn new things even on the “less secure” challenges. They are also the creators of MBE (which mainly covers x86)!
- Corelan Exploit Writing Tutorials (Free)
- If you’ve heard of Corelan you may know he is the author of mona.py. However, he does not rely on it when teaching you exploit development concepts, instead he teaches you how to find things manually. Once done, he introduces plugins and tools such as mona.py. To give you an idea when writing a ROP chain for an x86 exploit it may take you a couple hours, with mona.py it could be seconds… This should tell you enough as to why you should learn from these tutorials - the best part - they’re free! You may see that he targets Windows XP but SEH exploits still affect modern versions of Windows to this day… Just because the tutorial has not been maintained it does not mean it has lost its impact. Do not sleep on the free Corelan Tutorials… Although I have not taken it he also offers updated training for the Windows Stack if you do want the latest knowledge he provides and can afford it.
- Basics of Windows Shellcode Writing
- This is yet another free resource. Although it is one blog post, I have yet to see another resource such as this for shellcode development in Windows. If you study this and make an effort to understand it, I believe you will have the ability to write Windows shellcode! This is an important skill to have since exploits sometimes require custom stubs. In addition to this, you may have a hard time learning this skill on the fly since it is not as easy to write as it would be in a Linux environment. For this reason I recommend learning shellcoding BEFORE enrolling in the AWE.
- Evasion Techniques and Breaching Defenses (PEN-300)
- Although I never achieved the OSEP, I cannot deny that the way Offsec covers navigating the Windows API is excellent. If you can learn how to write programs using the Windows API without this course you can skip the PEN-300. Although it does also cover some malware development which easily falls into the category of exploit development since you’re often working with API calls and memory management.
- CodeMachine WINMAL
- This course is far more advanced that PEN-300, if you don’t already know how to program using the Windows API you will find this to be hard to follow. Regardless the techniques CodeMachine teaches are extremely beneficial. In fact this is a course I will be taking again (in addition to other trainings) and it is a course that I would say is worth re-taking anytime it is updated. You get no certification for completing this course, this is purely for obtaining knowledge… which is power.
- Corelan Heap Masterclass
- This course by Corelan is not free… However the knowledge is truly priceless and I guarantee if you pay attention even a little bit, it will directly impact your career. Shorty after attending, using the knowledge I obtained I was able to exploit a 0day on an x64 target having NEVER touched the architecture. This is because the techniques Corelan teaches are applicable to any architecture! If you followed my map - by now you are likely able to fully digest the information he will be teaching. As much as I hate to say it, at the time I took it, much of the information went over my head. However, the information that didn’t directly aided me during a real engagement. This is again a course worth re-taking when updated.
- HackSysVulnerableDriver (HEVD)
- I and many others offer free tutorials on how to exploit the HEVD driver. This is a solid entry into driver / kernel exploitation. By now you should be familiar with the bug classes you are likely to encounter. The bugs that exist in userland also exist within kernel! By now this should be a walk in the park for you!
- SANS 760
- This is an absolutely incredible course… The amount of information that is valuable to the modern exploit developer cannot be emphasized enough. However, if you lack a significant amount of knowledge much of the information will go over your head. If you followed my map the information should now be easier to digest. This is another course I recommend taking every time there is an update.
- Advanced Windows Exploitation (AWE)
- You simply cannot get OSEE without taking the AWE. Even if you obtain the OSEE this is a course worth retaking when updated. The knowledge it provides would take you a considerable amount of time to obtain on your own. There’s techniques shown that if I went in blind, it would take me months if not years to learn. What you are paying for (the same applies to 760) in this course is the hard work of the course authors making incredibly complex subjects “simple”. So if you think learning these concepts is hard, imagine if you were on your own… Although the goal as a researcher is to be independent, the truth is your favorite researcher likely depended on research from another researcher. A solid example of this is Violet Phosphorus, Offsec does not use this method to bypass SMEP, the way they do it - I would not have done myself ("different but same same"). The perspective they hold on how to approach modern mitigations is worth every penny and I imagine updates will include the latest methods.
Since I have actually consumed these resources, these are my recommendations that I feel I can vouch for. If you ever get a recommendation from me I have either engaged in the course or read the book!
Notably, we now live in the year 2025 where there’s a TON of free resources. So if you are unable to get into these courses my advice is to download the syllabus and google how to do everything mentioned within the syllabus. This is how I originally prepared for the OSCP and OSCE.
Ain’t No Rest for the Wicked #
The truth is that when it comes to Offensive Security Operations, the studying never stops and in my experience working as a Red Team Operator, Exploit Developer, and Researcher a diverse set of skills is expected from you by your employer. So, you’ll need to be advanced in multiple subject matters depending on your role.
This is where the AWE, Corelan Advanced, WINMAL, and SANS 760 shine, because luckily once you learn C, Assembly Language, and Reverse Engineering when a new techniques comes out you will be able to learn it relatively fast. Sadly, these new techniques are rarely documented in a manor that you would learn quickly - this is why I have a massive respect for course authors.
The huge value I see from these courses is the ability to get the techniques you will use in the field in a manor faster than it would take if you did on your own. Not only this, but you will get hands on experience implementing them which is also valuable. Which should you take when updated? That really depends on your role and expectations…
Regardless, never stop studying! A certification is a byproduct of the knowledge gained throughout the journey!
I also wanted to thank God my lord and savior Jesus Christ, I feel incredible blessed to be where I am today.
